The constant threat of cyber attacks is one of the biggest challenges hospitals face. Unfortunately, cyber attacks don’t stop during a global pandemic. Even during the worst health crisis in a century, hospitals must remain vigilant against cyber criminals. The past few months have seen several high profile cyber attacks on hospitals across the country, and just days before Halloween, the FBI and HHS issued a warning of “increased and imminent” cyber threats to hospitals.
In this blog, we’ll examine how cyber attacks have impacted the COVID-19 pandemic, some of the most common cyber attacks hospitals should prepare for, and methods for preparing for cyber attacks and addressing them when they happen.
Cyber Attacks in the Age of COVID-19
The COVID-19 pandemic has provided a prime opportunity for cyber criminals. A recent study by Check Point research found ransomware attacks doubled in Q3 compared to the first six months of 2020. While many industries fell victim to cyber attacks, the healthcare industry was the hardest hit. As Ekram Ahmed of Check Point told USA Today, that’s because healthcare organizations “are the most desperate and willing to pay.” It’s easy to see why.
While cyber attacks can have serious financial implications for any organization, cyber attacks targeting hospitals can have a real human cost as well. This proved true in September when a patient in Germany died as a result of a ransomware attack on a hospital in Düsseldorf. The hospital had been infected with ransomware, which caused its systems to crash and forced the hospital to turn away emergency patients. The female patient died due to treatment delays when she was taken to another hospital 20 miles away.
There are many examples of hospitals paying large sums to cyber criminals after being the victim of a cyber attack, but this is the first known occurrence of a patient dying as a result of a ransomware attack. At a time when hospitals worldwide are seeing record numbers of patient admissions and PPE shortages due to COVID-19, this tragic event underscores just how important cybersecurity is in healthcare.
Common Cyber Attacks
As technology has become more sophisticated, so have cyber attacks. Cyber criminals use a variety of tactics to try to infiltrate hospital systems. Some of the most common are:
- Ransomware
- Phishing
- Medical Device Hacking
Let’s take a deeper look at each type of attack.
Ransomware
One of the most common types of cyber attacks is ransomware. Ransomware is a type of malware that infiltrates a system and either encrypts sensitive data, such as financial information and patient records, or locks a user out of the system. The attacker solicits a ransom to decrypt the data or restore access to the user. Obviously this poses a huge risk to healthcare organizations since encrypted patient data or locked systems can delay crucial care.
One of the most famous examples of a ransomware attack on hospitals is the WannaCry attack in 2017. WannaCry exploited a Windows vulnerability to lock users out of systems. The ransomware attack affected 230,000 computers in hospitals across 150 countries, costing an estimated $4 billion globally. The United Kingdom was hit especially hard, with financial losses estimated at around the equivalent of $120 million.
For more information on ransomware, including nine more infamous ransomware attacks, check out Kasperky’s resources on the topic.
Phishing
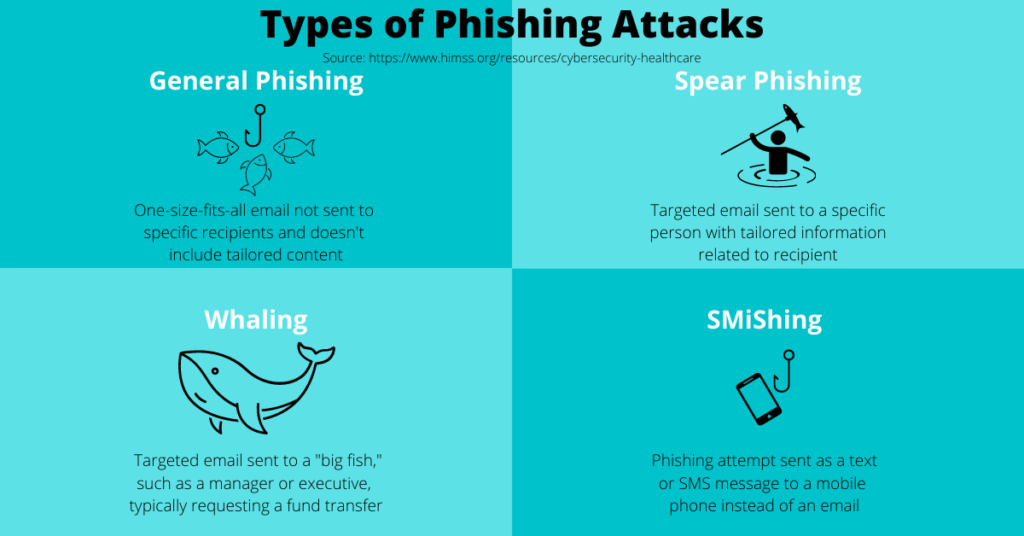
Phishing is one of the most common methods by which ransomware infiltrates a system. In a general sense, phishing is an attempt to steal a user’s credentials or get them to download malware by clicking a malicious link in an email or text message. In a phishing attempt, the attacker typically sends a vague message with a link or file that either installs malware on the user’s device when clicked or directs them to a webpage requesting them to enter sensitive information, such as login credentials. While phishing messages tend to be vague and littered with typos, cyber criminals have become more sophisticated over the years, using more targeted attempts. Types of phishing attempts include:
- General Phishing – a one-size-fits-all email that doesn’t target a specific individual and doesn’t contain tailored information such as the recipient’s name or title. General phishing emails are the easiest to spot.
- Spear Phishing – a targeted email sent to a specific person with tailored information related to the recipients, such as their name, job title, or job responsibilities.
- Whaling – a targeted email sent to a “big fish”, such as an executive or manager with access to financials and/or authority to direct payments. Whaling emails usually ask for a funds transfer and can result in substantial financial losses.
- SMiShing – a phishing attempt sent as a text or SMS message to a mobile device instead of an email.
With more healthcare employees working remotely as a result of the pandemic, phishing attempts are an even bigger concern for healthcare organizations.
Medical Device Hacking
One of the most troubling types of cyber attacks to emerge in recent years is the hacking of medical devices connected to the internet. While the internet of things (IoT) has led to innovative healthcare solutions that streamline and improve patient care, it also created a new avenue for cyber criminals to attack hospitals. For instance, the aforementioned WannaCry ransomware infected 1,200 diagnostic devices in 2017. Of particular note during the COVID-19 crisis is the vulnerability of ventilators. If a hacker gains access to one of these critical devices, it could quickly result in a patient’s death.
Not only can cyber criminals shut down or lock these medical devices themselves, but they can also use the infected devices to access the hospital’s broader network. This allows the hacker to spread malware and steal or encrypt data just as if an employee had clicked on a malicious link. The risks associated with ransomware, phishing, and medical device hacking make cybersecurity imperative for healthcare organizations. In the next section, we’ll go over some measures organizations can take to prevent cyber attacks, as well as deal with them when they occur.
Dealing with Cyber Attacks
Understanding the different types of cyber attacks is only half the battle. The other half is knowing how to deal with cyber attacks. There are two approaches of dealing with cyber attacks: proactive and reactive. The most ideal approach is to proactively prepare for potential cyber attacks. This involves having the right cybersecurity measures in place. However, no matter how robust your cybersecurity protocols are, there’s always a chance of a small vulnerability being exploited. This is where knowing how to react to a cyber attack when it occurs can save not only money, but lives.
Let’s take a look at some proactive and reactive measures organizations can use to deal with cyber attacks.
Proactive Preparedness
Having the proper cybersecurity protocols in place is the best defense against cyber attacks. As a result of the October 28 FBI and HHS warning of imminent cyber attacks, some hospitals are taking proactive measures to minimize their risk of being victimized by cyber criminals. Examples include Claxton-Hepburn Medical Center in Ogdensburg, NY preemptively shutting down its email servers and Morrisville, VT-based Copley Hospital automatically backing up patient data each night.
As part of their focus on cybersecurity during National Cybersecurity Month in October, HIMSS released a comprehensive cybersecurity guide. The guide covers a variety of cybersecurity topics, including some cybersecurity best practices to prevent cyber attacks. Two best practices for cybersecurity preparedness featured in HIMSS’s guide are cybersecurity risk assessments and having the right security controls in place. HIMSS recommends a long list of basic and advanced security controls, including:
- Anti-theft devices
- Anti-virus software
- Data backup/recovery & encryption
- Data loss prevention
- Disaster recovery plan
- Firewall
- Intrusion detection/prevention
- Multi-factor authentication
- Security awareness training
- Vulnerability scans

While the list of cybersecurity prevention measures may seem overwhelming, two of the most important are cybersecurity training and physical access controls. In the end, people are both an organization’s biggest strength and weakest link. A staff that is properly training on cybersecurity best practices and can recognize cyber threats makes it difficult for attackers to get through. Conversely, staff who lack proper training are more susceptible to clicking malicious links or providing credentials to cyber criminals. Equally important is ensuring physical access to data and computers is monitored and secure. Even if all other cybersecurity protocols are in place, an unlocked computer is all an attacker needs to gain access and wreak havoc.
Reacting When Disaster Strikes
No matter how vigilant an organization is in preparing for a cyber attack, there’s always a chance an attacker can slip through the cracks. As cyber criminals become more and more sophisticated in their attacks, new vulnerabilities may arise. While continual cyber vigilance is the best weapon against cyber attacks, having the proper protocols in place can help soften the blow of a successful attack.
In the event your organization falls victim to a cyber attack such as ransomware, here are three main actions you should take:
- Don’t pay the ransom – paying the ransom only emboldens cyber criminals and increases the likelihood they’ll strike again.
- Shut down computers immediately – shutting down computers as soon as a threat is detected can prevent data encryption and loss, which is exactly how a Colorado hospital thwarted a ransomware attack last Christmas. Having proper downtime protocols, such as paper records, in place can help keep the hospital running in the event computers must be temporarily shutdown.
- Restore data with backups – continuous data backup can be a lifesaver in the event of a cyber attack. With proper backups, there’s no need to pay a ransom.
For more tips on what to do in the event of a cyber attack, check out our blog featuring real-world examples of how hospitals have responded to crises ranging from natural disasters to pandemics to cyber attacks.
Vigilance Takes Teamwork
As medical staffs around the world continue fighting COVID-19, they must remain vigilant against the ever present threat of a cyber attack. While antivirus and threat detection software, data backup and encryption, and other cybersecurity controls are important, people are arguably the most important tool in the fight against cyber crime. According to HIMSS’ cybersecurity guide, key stakeholders in healthcare cybersecurity include:
- Executives
- Patients
- Staff
- Vendors
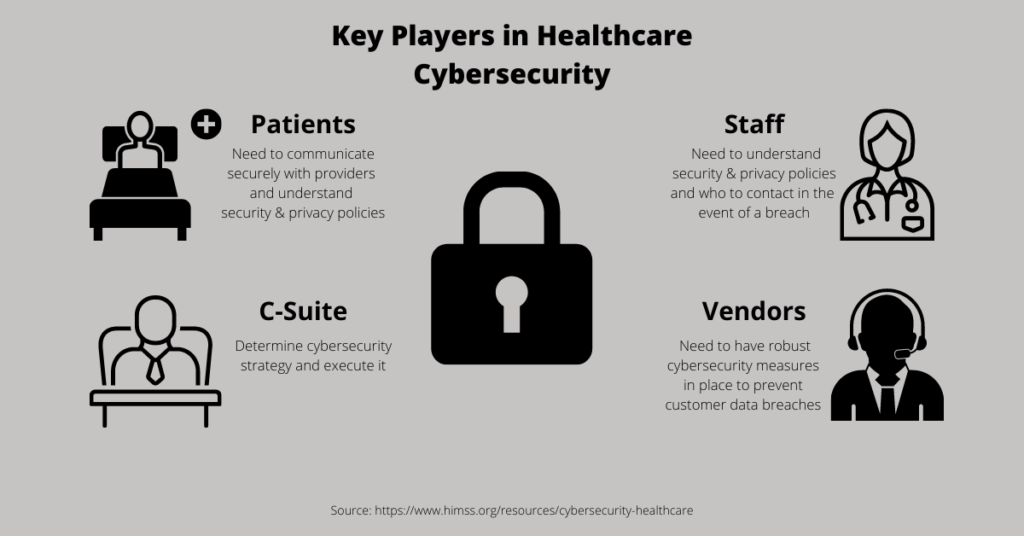
Executives should stay aware of the latest cyber threats and ways to prevent them. They are responsible for developing the hospital’s cybersecurity strategy and executing it. Patients should be educated on security and privacy policies and how to securely communicate with providers. Properly training staff on how to detect and avoid phishing attempts is a bedrock of cyber vigilance. Partnering with cyber vigilant technology vendors is equally important. In the event your system is compromised by a cyber attack, a cyber-aware vendor can make all the difference, something our customers know firsthand.
Whether a client is using our ambulatory order management solution, iOrder, or one of our radiology solutions such as NovaPACS, iPro customers have 24/7 customer support. The customer support team here at iPro has helped our customers deal with cyber attacks many times. Last December, an iPro customer support team member was conducting routine server maintenance for a 130-bed client with multiple locations across the southeast when he noticed the hospital’s PACS system had been compromised by ransomware. The support team member immediately notified the client (who was aware other systems had been infected, but not the PACS), and an iPro team member was dispatched to the site the very next day. Over the next 30 hours, the iPro team was able to rebuild the hospital’s 4 PACS servers, bringing the PACS back online before any other system and preventing 97% of the 90 million images stored on the PACS server from being encrypted. In conjunction with the hospital’s team and with the help of backup servers, the iPro team was able to recover the 3% of images that were encrypted as well.
In a similar situation, an iPro customer support team member was reviewing the weekly backup log for a 136-bed client and noticed the log had been flagged. Upon further investigation, he found signs the hospital’s system had been compromised and promptly notified the client. When Ryuk ransomware brought down a radiology group’s servers for several days, an iPro team member was onsite the same day and had the primary PACS server rebuilt with full images intact the same day.
Remaining cyber vigilant during the COVID-19 pandemic is of utmost importance. Having the proper security protocols and properly training staff to remain cyber vigilant are key to preventing cyber attacks. It also helps to know you’re not alone in the event an attack hits. That’s where partnering with a cyber vigilant technology vendor, like iPro, helps. To learn more about how we partner with you, check out our interactive partnership lifecycle diagram, or contact us today.




